In this post, I will show you how can you extract sensitive and juicy information from any image like when it was created, modified, what camera was used and a lot of other info.
This method could be useful for starting an Image forensic even though it would not enough for some forensic research but at least it can give a good start.
This can also be useful if you want to review your picture like what was the shutter speed, It’s copyright information, Camera Model.
This information can also be useful for the photographer if they want to find out what camera or settings were used for some particular photos.
What is Metadata?
Metadata provides information about other data. Its is simply a description of data. Metadata contains some elements described below;
- Who created it and when was it created
- Who last modified it and when was it modified
- Tags and its categories
- Who can access and update it
What is Exif Metadata?
Exif (Exchangeable Image Format) data shows information about your camera model, camera settings, ISO, exposure was used for taking a picture. Exif can also store on what date that picture was taken and it can also contain GPS location in it.
The most camera has these settings by default which lead to store some personal info that was never meant to expose. So the information stored in it is called Exif Metadata
Let’s Move to the steps of retrieving Exif Metadata
There are many ways to do this, but here I will be touching 4 methods.
Method 1# Retrieving Exif Metadata Using Command Line Tool
Step 1: Fire up your terminal and install perl exiftool by typing the below command
sudo apt install libimage-exiftool-perl
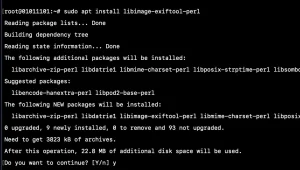
Step 2: Now run it by typing exiftool and your image location which you want to inspect. e.g the image I want to use an image stored in a folder of my Ubuntu VPS testing environment. See an example below
exiftool /home/username/http.xxxxx.xxxxx.com.png
And we got some data about the image as you can see in the screenshot below.
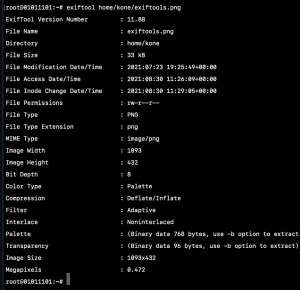
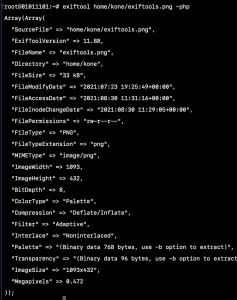
We can also export the output as php array for this just add -php after the command e.g
exiftool /home/username/http.xxxxx.xxxxx.com.png -php
Now you will get output like PHP array
There are a lot of ways to parse the output which you can test yourself. You can also get the metadata output in a binary format by using -b options after the command.
There are also many ways to parse the output formats. Check ExifTool documentation here.
Method 2# Use Ver Exif’s Web App
We can also use websites to extract metadata from EXIF images. there are two great websites to extract Exif data. But let’s start with Ver Exif. This web app discloses juicy data to us after a scan.
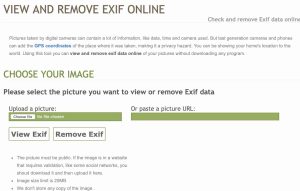
Also, this website allows us to remove metadata out of images. Removing the metadata is useful and helps improve our online privacy practices.
if you want to make sure an image you’re sending doesn’t contain data you didn’t intend to send. Then this web app can help you, but you can’t be going to this website all the time.
So I wrote a tip about removing Exif data from the image to improve online privacy.
To view Exif information with this site. upload a file or add its public URL, then hit “View Exif.”
In the image I used in the below screenshot is having few metadata, so the output is much less, you might have a huge data output. Which can contain Geo metadata also.
And the information gotten from this website is accurate.
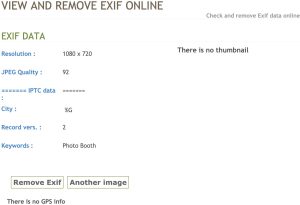
So now I clicked the “Remove Exif” data option and got the image downloaded.
Now let’s re-upload the image to see if the metadata is truly removed. it looks like it did remove something, but not sure it removed it all.
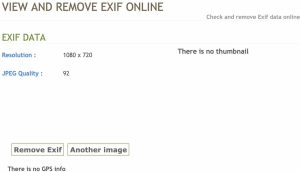
So let’s visit exifinfo.org to check, and you can see it still has few data. So I won’t recommend you use the tool to remove Exif data.
Method 3# Use Jeffrey’s Image Metadata Viewer Web App
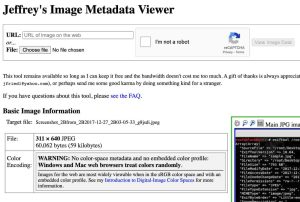
We can also use websites to extract metadata from EXIF images. We are going to start with Jeffrey Friedl’s Image Metadata Viewer over at exif.regex.info.
Unfortunately, the site does not use HTTPS. But don’t panic, it’s safe, you can see the simple design is easy to use and supports a vast variety of image formats.
Just like other methods, you can view EXIF data of any image you want.
So you can scan RAW images files like CR2 and DNG, PNG, and TIFF, to name a few. Upload a file or add its public URL, check the CAPTCHA, and hit “View Image Data.” And you see the Exif data that the image you upload is carrying.
Method 4# Use the EXIF Viewer Chrome Extension
In your Google Chrome Browser, you will have to install the EXIF Viewer extension, Having this extension installed and activated. You will be able to pull up the Exif data of any photo that’s load in your browser.
Browser add-ons for viewing Exif data seems to be easier and fast that the web-based tool or command line.
When you are done installing and enabling the plug-in. You can now right-click on any image in the browser and select “Show EXIF data” to reveal any information the image is carrying.
Let’s test this out, I found an image on image on a website and looked through the metadata provided by EXIF Viewer to find if the image carries any data that might speak about the website owner.
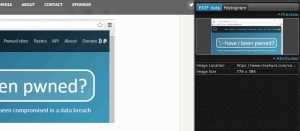
How can you track users location using EXIF metadata?
The image carries a lot of data about people, that’s why its advisable not to share many things online. You image alone is enough to get where you stay. So let’s see how we can find someone location using the image they shared.
Step1: Get the image of the person you want to find the geolocation in their picture
Step2: Then you can use any of the method above to extract the EXIF data in the image.
Step3: Look closely to see if you have GPS Lat and Long data in the Exif data, just like this
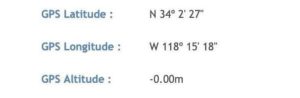
Step4: Copy the GPS Latitude and Longitude codes and paste them in your google map search box.
It will show you the exact location that the user took the picture.
I hope you enjoyed this guide to extracting hidden metadata from image files! If you have any questions on image OSINT. Feel free to comment below.






This wont work though on images received via the most popular means, ie: Whatsapp, Telegram, instagram or facebook right?
It works, if the platforms are not removing the exif, works well with facebook, IG, Twitter not sure of whatsapp, but if the images was sent directly to you, it should work